This post is the fourth in a series where I introduce concepts and considerations for security in Microsoft SharePoint 2013. These articles serve as an introduction to those new to SharePoint or to those that have SharePoint up and running but are looking at built-in features and third-party solutions to secure their sensitive information.
Understanding Security Scopes and their Limits
Understanding SharePoint permissions and using them effectively means you need to understand the concept of "security scopes" and their limits. When unique permissions are assigned to a container or item,
SharePoint creates what is called a security scope. This is an important
concept to understand because there are limits to how many security scopes can
be created, and there are limits to the size of the security scope before
SharePoint performance starts to be adversely affected.
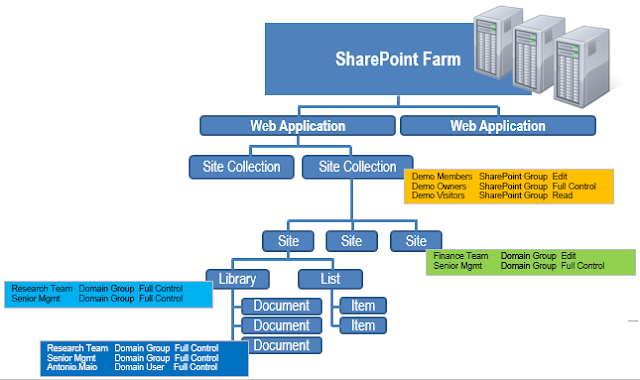
Each site collection initially contains one (1) security scope,
related to the initial permissions at the site collection level. Each time
permission inheritance is broken a new security scope is created. So, in Figure
1 above, the “Demo” site collection has four security scopes: one at the site
collection level, another at the site level, another on a library, and a fourth
on a document. All other sites, libraries, documents and items in the diagram
inherit their permissions and therefore no security scope is created for those
levels. The size of the security scope refers to the number of principals in
the security scope. Remember, a principle is a user, group or claim. To view
another example, refer to Figure 2 below to see how security scopes are created
as permission inheritance is broken.
In previous versions of SharePoint, there were various limits documented around how many security scopes a library or list should contain before performance would be adversely affected. These numbers tended to vary depending on the article and there was a lot misunderstanding around them. In SharePoint 2013, each list or library can contain up to 50,000 security scopes before performance begins to be impacted (this change actually came about in SharePoint 2010, Service Pack 1 and the latest cumulative updates, but it has only been documented in SharePoint 2013). This is a significant improvement over previous versions and when you think about it, it’s a very large number to work with. This means that a single library can have up to 50,000 documents or items which each have their own unique permissions. In addition to this, a library can also contain other documents which inherit permissions from the library level (or site or site collection).
In order to actually create unique permissions on up to 50,000
documents or items in a library/list, a SharePoint farm administrator must
adjust a setting called the “List View Threshold”. Modification of this setting
requires these steps:
1.
Log into the SharePoint Central
Administration console
2.
Click “Application Management” on
the left hand side, then click “Manage Web Applications”
3.
Select the web application you
wish to modify
4.
In the ribbon click “General
Settings” to activate the menu
5.
In the menu select “Resource
Throttling”
6.
Find the “List View Threshold”
setting and modify it to the appropriate value (the default is 5000)
If you do plan to modify this setting to support more unique permissions, ensure that your environment is sized appropriately to handle the additional query load. As well, ensure that you test your environment under realistic conditions with this setting in place to ensure that users will not be affected by potential performance issues.
Another important limit to understand in SharePoint is the size of
the security scope. The size of a
security scope refers to the number of users or groups assigned with unique
permissions for a particular scope. Limits on this size have remained consistent
between SharePoint 2010 and SharePoint 2013. Each security scope can contain a
maximum of 5000 principles. This means, each time you specify unique
permissions on an item or document there can be no more than 5000 users, groups
or claims specified. Once again, in reality this is quite a large number to
work with.
These limits of course depend on the architecture of your SharePoint
2013 farm and the hardware/configuration used. For more information on
SharePoint 2013 boundaries and limits please refer to the following Microsoft
article:
Limited Access Permissions
When permission inheritance is broken and unique permissions
assigned to a particular item, let’s say a document, SharePoint will
automatically create what is called a ‘Limited Access” permission on its parent
and all the way up the hierarchy up to the root site collection. The Limited
Access permission will contain the same principles (users, groups and claims)
as the unique permission assigned, however using the pre-defined Limited Access
permission level. The purpose of this Limited Access permission is to give the
user just enough permissions to navigate to the item on which they were just granted
permissions (even if they did not have access to the folder, library or site
previously). This occurs automatically, as part of the process of assigning
unique permissions.
The challenge with Limited Access permissions is that they never get
removed or cleaned up in any automated way. Even if you cause a particular
document or item to re-inherit permissions from its parent library, the limited
access permissions will remain in place. Therefore, it is important to monitor
how many Limited Access permissions are created because this does contribute to
the limits discussed in the previous section.
The following diagram illustrates how security scopes and Limited
Access permissions are created:
Figure 2. SharePoint security scopes are created when permission
inheritance is broken.
There has been quite a bit of literature written in recent years about security scopes and their limits, not all of it accurate. I highly recommend that you review the latest document from Microsoft (link above) on the limits in SharePoint 2013 because that will be the most up to date documentation.
There has been quite a bit of literature written in recent years about security scopes and their limits, not all of it accurate. I highly recommend that you review the latest document from Microsoft (link above) on the limits in SharePoint 2013 because that will be the most up to date documentation.
-Antonio